Hack-The-Planet Podcast: Episode 1
host GIT repositories painlessly
As people around me discuss what to go for in regards to manage their growing number of private GIT repositories I joined their discussion.
A couple of years ago I assessed how I would want to store my collection of almost 100 GIT private repositories and all those cloned mirrors I want to keep for archival and sentimental reasons.
An option was to pay for GitHub. Another option, which most seemed to prefer, was going for a local Gitlab set-up.
All seemed not desirable. Like chaining my workflows to GitHub as a provider or adopting a new hobby to operate and maintain a private GitLab server. And as it might have become easier to operate a GitLab server with the introduction of container management systems. But I’ve always seemed to have to update to a new version when I actually wanted to use it.
So this was when I had to make the call for my own set-up about 4 years ago. We were using a rather well working GitLab set-up for work back then. But it all seemed overkill to me also back then.
So I found: gogs.io
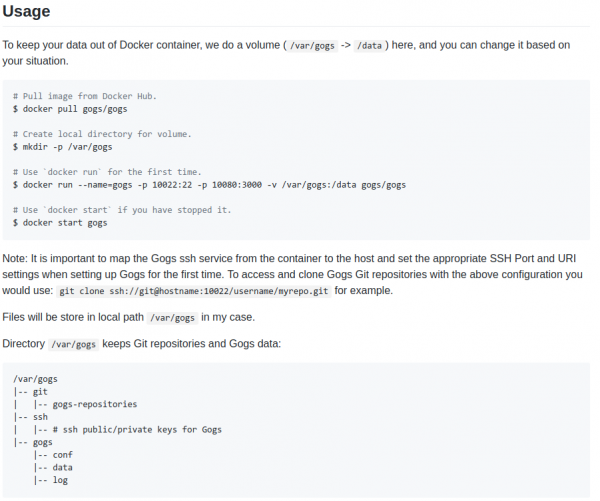
It runs with one command, the only dependency is two file system directories with (a) the settings of gogs and (b) your repositories.
It’ll deploy as literally a SINGLE BINARY without any other things to consider. With the provided dockerfile you are up and running in seconds.
It has never let me down. It’s running and providing it’s service. And that’s the end of it.
I am using it, as said, for 95 private repositories and a lot of additionally mirrored GIT repositories. Gogs will support you by keeping those mirrors in sync for you in the background. It’s even multi-user multi-organization.
Train Melody / 武蔵小杉駅
In hearing distance of the place I am usually staying when in Tokyo is a train station. So if the wind is right and the window is open I hear all these train station chimes and sounds.
If you don’t know what it is, let Wikipedia educate you:
A train melody is a succession of musically expressive tones played when a train is arriving at or about to depart from a train station. As part of train passenger operations, a train melody includes a parade of single notes organized to follow each other rhythmically to form a lilting, singular musical thought.
In Japan, departing train melodies are arranged to invoke a relief feeling in a train passenger after sitting down and moving with the departing train. In contrast, arriving train melodies are configured to cause alertness, such as to help travelers shake off sleepiness experienced by morning commuters.
発車メロディ
With this post I also want to have you hear what I mean. These sounds are having interesting pavlovian effects anyways.
Hack-The-Planet Podcast: Episode 0
A friend of mine started something and I have the honor to be part of it. The world now has one additional podcast to listen to. It’s in german though. For now at least.
We are still working on the website, the feed and the audio mixing and recording quality. So bear with us.
And now: Episode 0 is upon us!
Discover Zaraday!
Prickle-Prickle 5 Bureaucracy: The Apostle Zarathud’s Holyday. A hard nosed Hermit of Medieval Europe and Chaosphe Bible Banger (after his enlightenment, that is). Dubbed “Offender of The Faith”. Discovered the Five Commandments (The Pentabarf).
Zaraday
˙sǝᴉʇᴉʌᴉʇɔɐ ǝʇɐᴉɹdoɹddɐuᴉ ǝpnlɔuᴉ sǝᴉʇᴉʌᴉʇɔɐ ǝʇɐᴉɹdoɹdd∀
CCCamp 2019 session schedule is available
Celebrate Multiversal Underwear Day
Expose your undies! Celebrate by wearing nothing but unmentionables in public, or at least by wearing your underwear, or somebody else’s, where people can see it so they can gawk at you. (This is a great day to apply for membership in the Lesser Disorder of Underwear Heads.)
Multiversal Underwear Day
グランツリー武蔵小杉 and Park City Forest Towers in daylight
Celebrate Confueye
The 73rd and Last Day of the Season of Confusion. Eye Day is celebrated by playing Discordian Games.
Confusion
electronic fireworks
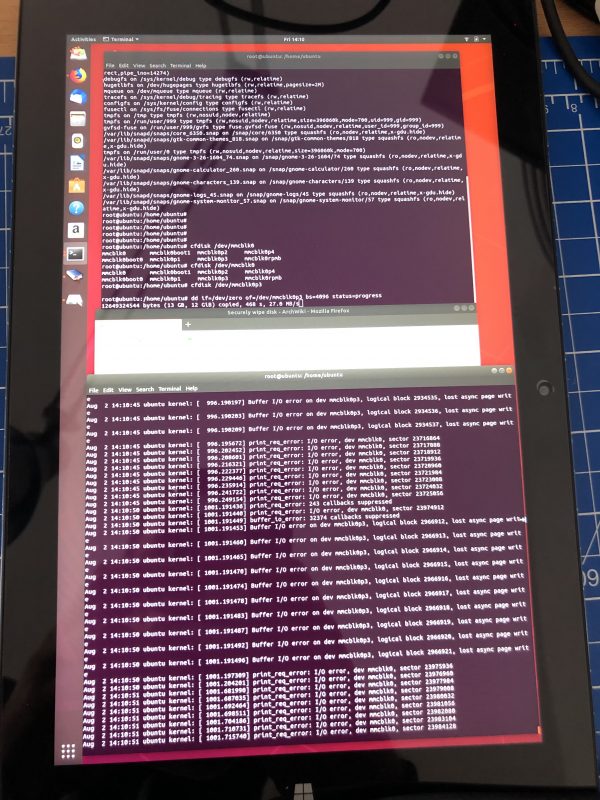
The firecracker exploded. Apparently after 2 weeks of usage of the Chuwi Hi10 Air the eMMC flash is malfunctioning.
In a totally strange way: Every byte on the eMMC can be read, seemingly. Even Windows 10 boots. But after a while it will hang and blue screen. Apparently because it tries to write to the eMMC and when those writes fail and pile up in the caches at some point the system calls it quits.
Anyhow: It means that no byte that is right now on this eMMC can be deleted / overwritten but only be read.
The great chinese support is really helpful and offered to replace the device free of charge right away. That’s very nice! But I came to the conclusion that I cannot send the device in, because:
It contains a full set of synched private data that I cannot remove by all means because the freaking soldered-on eMMC flash is broken.
The recipient of this broken tablet in china would be able to read all my data and I could not do anything about it.
Only an extremely small fraction of data is on there unencrypted. Only that much I hadn’t yet switched on encryption on during the initial set-up I was still doing on the device. And that little piece of data already is what won’t let me send out the device.
Now, what can we learn from this? We can learn: Never ever ever work with anything, even during set-up, without full encryption.
Es ist egal, aber
Tocotronic is one of the bands I listened to during my teens/twenties. That dates me, that dates the band.
It’s very german. You’ll find their music on most streaming platforms. I recommend starting with the albums “wir kommen um uns zu beschweren” and “es ist egal aber”.
Anyhow. Now one member of the band starts a podcast!
Jan Müller ist seit über 25 Jahren Mitglied der Band Tocotronic. Er ist mit dem Format des Interviews bestens vertraut und kann sich als Fragender gut in die Perspektive seiner Gäste hineinversetzen. Die persönliche Auswahl seiner Gesprächspartner*innen bildet die Grundlage für authentische Gespräche, die stets von Interesse und Respekt geprägt sind. Mit “Reflektor” startet Jan seinen ersten Podcast.
https://viertausendhertz.de/reflektor
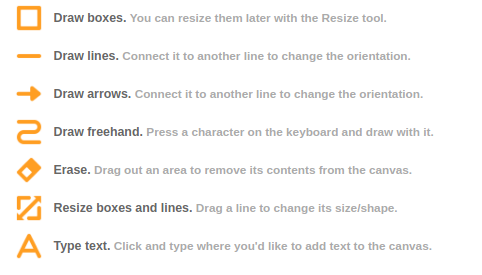
easily draw text based flowcharts
As I am mainly producing text and markdown notes throughout the day I am always interested in ways to quickly create simple text-based flow-charts.
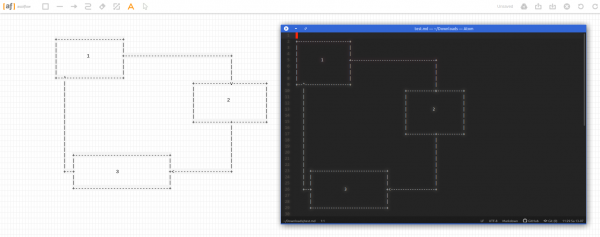
I did write about a couple of tools to accomplish this previously but I want to take note of the most recent addition to the toolbox: ASCIIFlow Infinity.
You open it in your browser and start drawing with the simple tools provided.
When you are done you export it to plain text and do what you feel like with it.
Here’s a feature overview:
train sounds in Japan
If you’ve ever been to Japan you must have noticed that everything and anything makes sounds and talks. Elevators, escalators, doors, train stations, gates, vending machines – you name it, it makes sounds and talks.
It’s so apparent but yet quite comforting that I enjoyed it. It became an additional channel of information without the need of point-and-call all the time. Highly effective for me.
Japan utilizes sounds to a degree that every detail seems to count. Take the station gates you rush through to get to your train platform. It’ll sound differently depending on how you pay, what status your ticket had and even how close your IC-cards balance is to being empty.
Or just the fact that the ticket gates make sounds at all to make you find them easily.
A good portion of this sounds you can find on places like YouTube or specialized websites. One of those specialized websites is hatsumelo.com:
For some routes and stations you find here:
- Station melody – departing and arrival melodies that are played on the occasion
- In-car chime – chimes played before and after information broadcasts mainly in the Shinkansen and limited express trains.
- Door opening and closing – doors make sounds too!
brain simulators
With recent announcements around human brain and brain-machine interface research like Neuralink the topic is seemingly seeing some more investments now.
As this whole topic is special to my heart I am interested in all things brain simulations. Thus here’s my personal “logbook entry” on the re-appearance of this topic:
This leads to one of the arguments for whole-brain simulation: it’ll help us solve the “biological imitation game,” a Turing test-like assay that pits digitally reconstructed brains against real ones. Iterations of the test help select increasingly more accurate models for a given task, which eventually become the most promising ideas for how specific biological networks operate. And because these models are based on mathematical equations, they could become the heart of next-generation AI.
Singularity Hub
There’s also a paper! – Unfortunately I cannot link directly to the paper as it is behind paywalls. Neuralink on the other side was so kind to publish open-access:
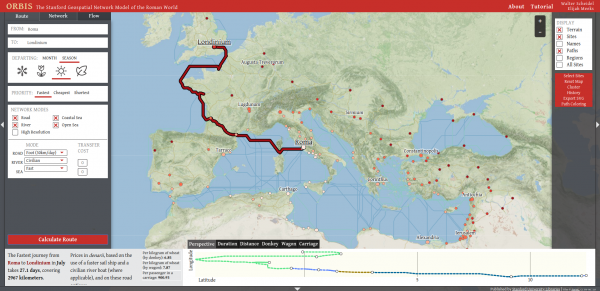
The Fastest journey from Roma to Londinium..
…in July takes 27.1 days, covering 2967 kilometers. At least if you would have taken the challenge in times of the Roman Empire.
ORBIS: The Stanford Geospatial Network Model of the Roman World reconstructs the time cost and financial expense associated with a wide range of different types of travel in antiquity. The model is based on a simplified version of the giant network of cities, roads, rivers and sea lanes that framed movement across the Roman Empire. It broadly reflects conditions around 200 CE but also covers a few sites and roads created in late antiquity.
ORBIS: The Stanford Geospatial Network Model of the Roman World
By simulating movement along the principal routes of the Roman road network, the main navigable rivers, and hundreds of sea routes in the Mediterranean, Black Sea and coastal Atlantic, this interactive model reconstructs the duration and financial cost of travel in antiquity.
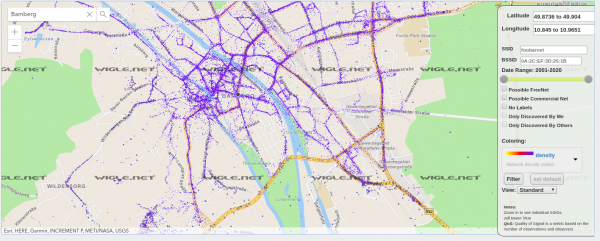
Wireless Network Mapping – data source and data sink
When you work with wireless networks and you do programming and mobile app development that works with things like user location you might find this useful.
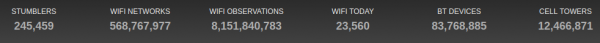
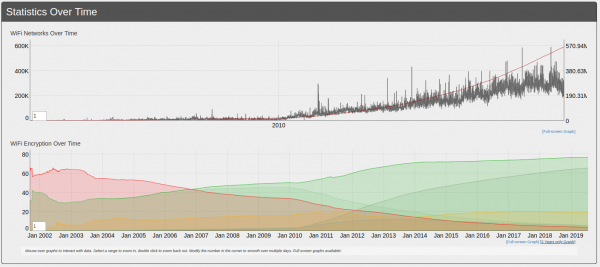
Take thousands of users and you’ve got the worlds wifi networks mapped…
WiGGLE (Wireless Geographic Logging Engine) is a project which takes wireless network data + location and puts it into a big database. On top of storage it’s giving you access to that data.
We consolidate location and information of wireless networks world-wide to a central database, and have user-friendly desktop and web applications that can map, query and update the database via the web.
https://wigle.net/faq
So what’s my use-case? Apart from the obvious I will make use of this by finding out more about those fellow travelers around me. Many people probably to the same as me: Travel with a small wifi / 4g access point. Whenever this accesspoints shows up in scans the path will be traceable.
I am curious to see which access point around me is in the million-mile club yet…
full website screenshots from your commandline
Think of this: You want to capture a whole, multi-scroll-pages, web-page into one image.
This can be difficult without the right tools. It surely will be a lot of work to accomplish a 10th of thousand pixel height screenshot put together from multiple single screenshots…
CutyCapt is there to help! It’s a command line tool encapsulating the very powerful WebKit browser engine to render a full page and then create a single file screenshot of the whole page for you.
By example, this is what it did when told to screenshot this website:
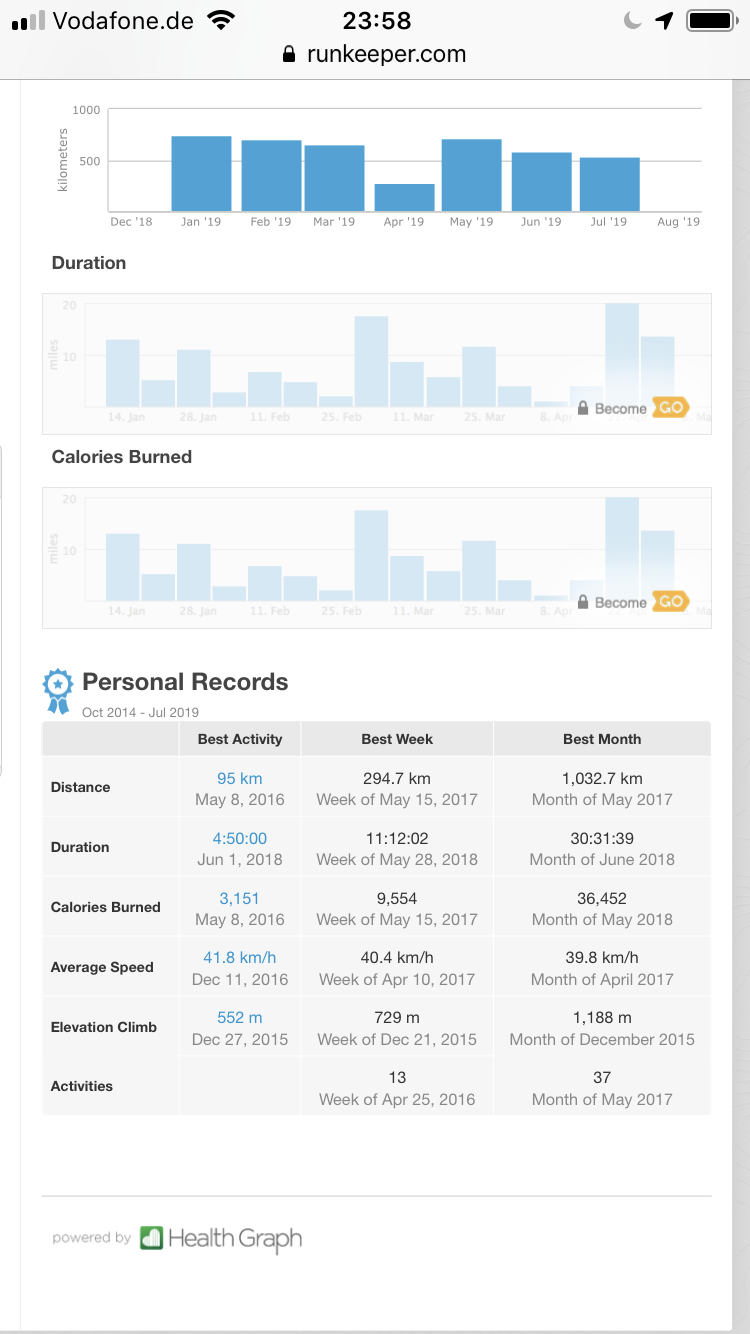
4 years of sports
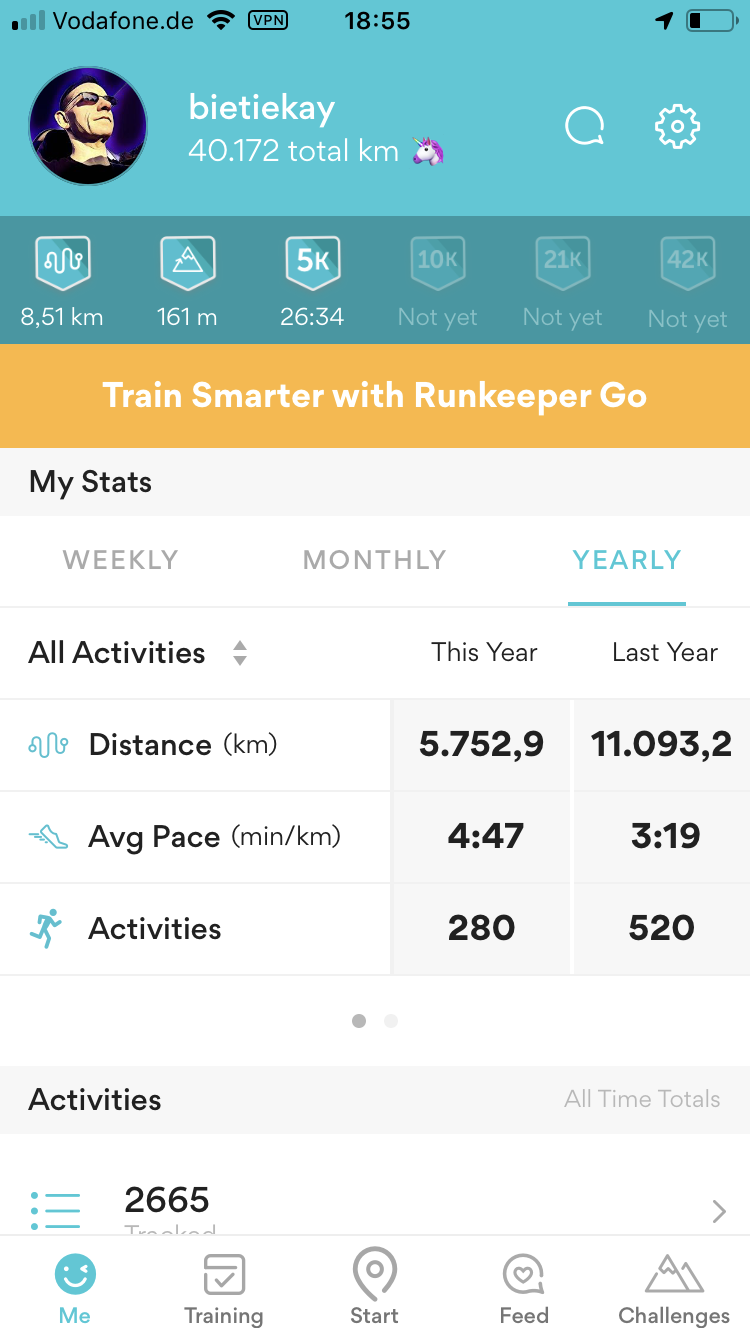
Addition: Of course the app I am using is called runkeeper yet I am mostly doing cycling. On average I am actually doing about 30km every day right before work starts. Here’s an additional statistic just for cycling:
PixelFed – Federated Image Sharing
In search of alternatives to the traditional centralized hosted social networks a lot of smart people have started to put time and thought into what is called “the-federation”.
The Federation refers to a global social network composed of nodes that talk to each other. Each of them is an installation of software which supports one of the federated social web protocols.
What is The Federation?
You may already have heard about projects like Mastodon, Diaspora*, Matrix (Synapse) and others.
The PixelFed project seems to gain some traction as apparently the first documentation and sources are made available.
PixelFed is a federated social image sharing platform, similar to instagram. Federation is done using the ActivityPub protocol, which is used by Mastodon, PeerTube, Pleroma, and more. Through ActivityPub PixelFed can share and interact with these platforms, as well as other instances of PixelFed.
the-federation
I am posting this here as to my personal logbook.
Given that there’s already a Dockerfile I will give it a try as soon as possible.
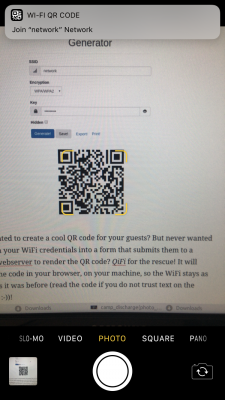
WiFi QR Code Generator
Whenever we arrive at a place that we have not been before it is important to get properly connected to the internet.
Finding wifi SSIDs and typing passwords is tedious and prone to errors. There is an easier way of course!
The owner of the wireless network can generate a QR code that you can easily take a photo of and your phone will automatically prompt you to log into the wireless network without you having to type anything.
On your phone it looks like this:
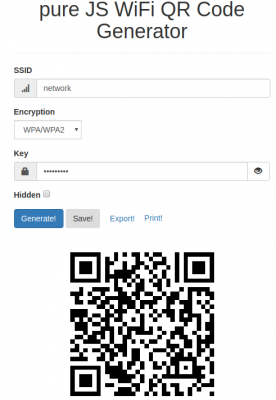
To generate these QR codes that contain all information for visitors/new users to connect this simple tool / online generator can be used:
Ever wanted to create a cool QR code for your guests? But never wanted to type in your WiFi credentials into a form that submits them to a remote webserver to render the QR code? QiFi for the rescue! It will render the code in your browser, on your machine, so the WiFi stays as secure as it was before (read the code if you do not trust text on the internet :-))!
Qifi.org
Don’t worry: your access point information is not transferred over the internet. As this is open source at the time of writing the data was held in HTML 5 local storage on the local browser only and not transferred out.
Remember Mal-2 Day
Sweetmorn 55 Confusion: Remembering the Life and Words of Malaclypse the Younger, who left us on this day in 3166 YOLD (2000 AD).
Pen Input
CCCamp 2019 – 21. – 25. August 2019
The Chaos Communication Camp is an international, five-day open-air event for hackers and associated life-forms. It provides a relaxed atmosphere for free exchange of technical, social, and political ideas. The Camp has everything you need: power, internet, food and fun. Bring your tent and participate!
CCCamp 2019 Wiki
It has been 2005 that I had the time and chance to attend an international open-air meeting of normal people. Of course I am talking about the 2005 What-the-hack I wrote about back then.
This year it’s time again for the Chaos Communication Camp in Germany. Sadly still I won’t be attending. Clearly that needs to change with one of the next iterations. With the CCC events becoming highly valuable also for families maybe it’s a chance in the future to meet up with old and valued friends (wink-wink Andreas Heil).
The Chaos Communication Camp (also known as CCCamp) is an international meeting of hackers that takes place every four years, organized by the Chaos Computer Club (CCC). So far all CCCamps have been held near Berlin, Germany.
The camp is an event for providing information about technical and societal issues, such as privacy, freedom of information and data security. Hosted speeches are held in big tents and conducted in English as well as German. Each participant may pitch a tent and connect to a fast internet connection and power.
Enjoy the intro-movie that has just been made available to us, alongside the whole design material:
electronic firecracker: Chuwi Hi10 AIR Tablet
The Android tablets I am using for my kitchen scale display and for myfitnesspal data-entry are aging quite bad and apart from the near-display death of one of the tablets both are not supported and updated anymore.
Using them therefore poses an increasing risk. After one of them almost died on me I was determined to replace them both. Looking at alternatives at the lowest possible price quickly showed that I am not going to get another Android tablet.
Instead I was ready to give a chinese company a chance:
I ordered it on 24th of June and it was delivered today. All in all I’ve paid 136 Euro for the tablet and 45 Euro for the keyboard attachement.
Despite the ridiculously low price this thing is quite impressive. It’s sporting a fast-enough Intel Atom processor with 1.4 ghz and 4 Gbyte of RAM. The 64 Gb of solid-state storage where quickly upgraded by an additional 400 Gb MicroSD card for local data storage.
As of writing this it’s still installing and updating the Windows 10 to 1903 but so far I am beyond impressed.
I’ll write more about the device when I’ve had more time to use it. One word for the keyboard attachement: the keyboard is good-enough. Not great but better than for example that on the Pinebook. The touchpad is very small but works – the thing has a Touchscreen anyway.
bridge the openvpn-status.log to MQTT
For big parts of my VPN needs I use OpenVPN. Especially on iOS devices the deep integration just works. Even to a degree that you enable the VPN once and the device will transparently keep it up / reestablish connections when required.
OpenVPN protocol has emerged to establish itself as a de- facto standard in the open source networking space with over 50 million downloads. OpenVPN is entirely a community-supported OSS project which uses the GPL license.
VISIT THE OPENVPN COMMUNITY
I am using the dockerized version of OpenVPN. From there I’ve got several ways to get telemetry data (like connections, traffic, …) out of it. One way is the management interface provided by OpenVPN. Another way is by using the default openvpn-status.log file.
Since the easiest way out-of-the-box was to use the logfile I sat down and wrote a little 2mqtt bridge for the contents of the logfile.
It’s also dockerized so you can easily set it up by pointing the openvpn-status.log to the right volume/mount-point.
When done it’ll produce MQTT messages like this:
The set-up and start-up is rather simple:
docker run -d --restart=always --volume /openvpnstatus2mqttconfiglocation/:/configuration --volume /openvpnstatusloglocation/:/openvpn openvpn-status2mqttMQTT Broker, Topic-Prefix and so on are configured with the .json configuration file found along the project.
Of course everything I wrote is available on GitHub as open-source.
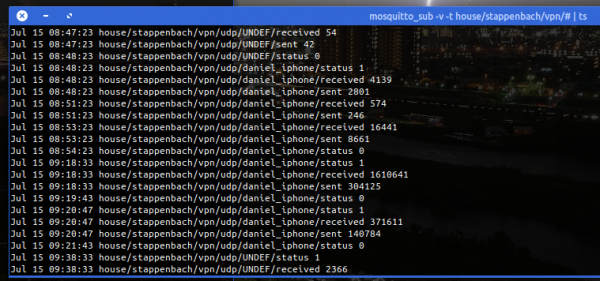
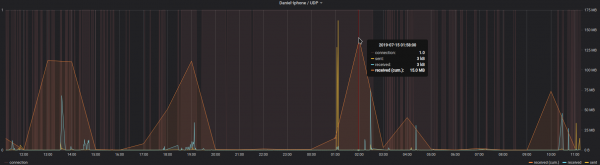
The immediate outcome of this is that with the always-on VPN I am now getting statistics about, for example, the data consumption of my iPhone.
The big traffic spike at 1 AM is the backup that my iPhone does every night. Very interesting also how often the connection is closed and opened again even without me using the phone…
Celebrate Confluflux
terminates the calling process if buffer is not a valid userspace pointer.
How to build security into your software? It’s always simple to find examples where things gone wrong. Where security was compromised and things did not work out as the software authors envisioned.
As always there are new concepts and operating systems being implemented.
A particularly interesting example of security software design can be observed here:
Fuchsia is an open source capability-based operating system currently being developed by Google.
In contrast to prior Google-developed operating systems such as Chrome OS and Android, which are based on the Linux kernel, Fuchsia is based on a new microkernel called Zircon. The name Zircon refers to the mineral of the same name.
Google Fuchsia
So you now know what Fuchsia is. Now on to the actual example. For this we have to take a look into the developer documentation of Zircon:
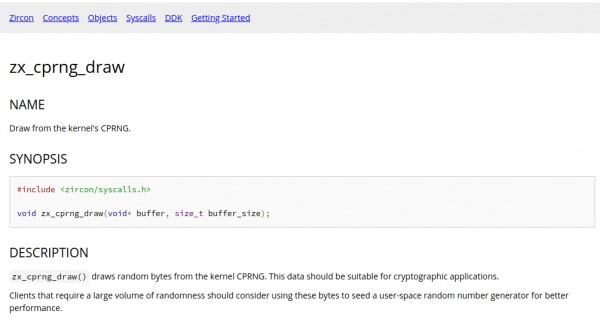
So this describes a method to get random numbers from the systems cryptocraphically-secure-random-number-generator (CPRNG). It takes a pointer to a memory location as a parameter.
Now. What’s secure about that? It’s the behaviour of the method when it is encountering an unsecure situation:
It’ll kill the calling process when the pointer is not valid.
a red triangle on the window
When you walk around in Tokyo you will find that many buildings have red-triangle markings on some of the windows / panels on the outside.
I noticed them as well but I could not think of an explanation. Digging for information brought up this:
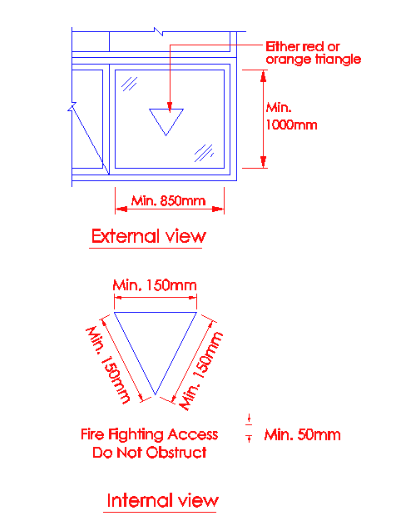
Panels to fire access openings shall be indicated with either a red or orange triangle of equal sides (minimum 150mm on each side), which can be upright or inverted, on the external side of the wall and with the wordings “Firefighting Access – Do Not Obstruct” of at least 25mm height on the internal side.
Singapore Firefighting Guide 2018
The red triangles on the buildings/hotel windows in Japan are the rescue paths to be used in case of fire. All fire fighters know the meaning of this red triangle on the windows. Red in color makes it prominent, to be located easily by the fire fighters in case of a fire incident. During a fire incident, windows are generally broken to allow for smoke and other gases to come out of the building.
Triangles in Japan
what do you do with a rental car?
“The only thing we can say is that data show a number of people rent cars without driving them.”
Growing number of car-sharing users don’t rent cars for driving
Wait. What?
“Usually the only place I can take a nap while visiting my clients is a cybercafe in front of the station, but renting a car to sleep in is just a few hundred yen (several dollars), almost the same as staying in the cybercafe.”
Growing number of car-sharing users don’t rent cars for driving
Right…
automated downloads
Hmm… I’ve set-up a script to automatically download a TV show about a year ago and just remembered it…
Apparently 1 year of this show is 167 Gbyte…
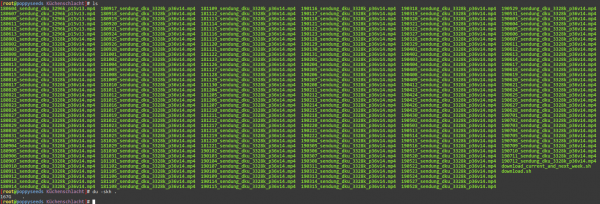
For completeness the download script – ignore my bad scripting:
#!/bin/bash
# parameter 1: month
# parameter 2: from day
# parameter 3: to day
# parameter 4: year
# data -dmonday +%d
next_monday=$(date -dmonday +%d)
next_monday_month=$(date -dmonday +%m)
next_monday_year=$(date -dmonday +%y)
previous_monday=$(date -d'monday-7 days' +%d)
previous_monday_month=$(date -d'monday-7 days' +%m)
previous_monday_year=$(date -d'monday-7 days' +%y)
next_friday=$(date -dfriday +%d)
next_friday_month=$(date -dfriday +%m)
next_friday_year=$(date -dfriday +%y)
previous_friday=$(date -d'friday-7 days' +%d)
previous_friday_month=$(date -d'friday-7 days' +%m)
previous_friday_year=$(date -d'friday-7 days' +%y)
for i in `seq 1 7`;
do
day=$(date -d'today+'$i' days' +%d)
month=$(date -d'today+'$i' days' +%m)
year=$(date -d'today+'$i' days' +%y)
wget -c "https://rodlzdf-a.akamaihd.net/none/zdf/"$year"/"$month"/"$year$month$day"_sendung_dku/1/"$year$month$day"_sendung_dku_3328k_p36v14.mp4"
done
IP-over-DNS
Picture yourself in this situation. You connect to a network and nothing works. Except for this:
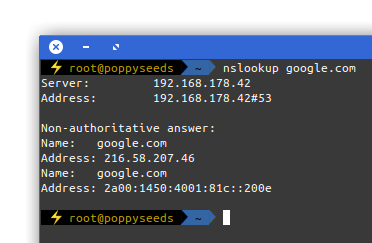
It is quite common to have DNS working in networks while everything else is not. Sometimes the network requires a log-in to give you access to a small portion of the internet.
Now, with the help of a tool called iodine, you can get access to the full internet with only DNS working in your current network:
iodine lets you tunnel IPv4 data through a DNS server. This can be usable in different situations where internet access is firewalled, but DNS queries are allowed.
It runs on Linux, Mac OS X, FreeBSD, NetBSD, OpenBSD and Windows and needs a TUN/TAP device. The bandwidth is asymmetrical with limited upstream and up to 1 Mbit/s downstream.
iodine
Setting it up is a bit of work but given that you are anyway having access to a well connected server on the free portion of the internet it can be easily done.
Of course the source is on github.
Decoding history, the hard way (and with machine learning)
Imagine you’ve got this ancient piece of technology in front of you. You clearly understand how the hardware works and you are even able to emulate the hardware on your modern-world computer.
Unfortunately hardware is only one half of the story. Software is the other half. And software at this time of the past was burned into chips which do not easily give their secret software away.
But let’s start with the hardware:
The IBM 5100 Portable Computer is a portable computer (one of the first) introduced in September 1975, six years before the IBM Personal Computer. It was the evolution of a prototype called the SCAMP (Special Computer APL Machine Portable) that was developed at the IBM Palo Alto Scientific Center in 1973. In January 1978, IBM announced the IBM 5110, its larger cousin, and in February 1980 IBM announced the IBM 5120. The 5100 was withdrawn in March 1982.
When the IBM PC was introduced in 1981, it was originally designated as the IBM 5150, putting it in the “5100” series, though its architecture was not directly descended from the IBM 5100.
And now on to the software:
The IBM 5100 portable computer came with some of its built-in programs stored in a read-only memory called the “non-executable ROS”. (ROS = “read-only storage”.) In contrast with the “executable ROS”, which supplies instructions to the 5100’s processor directly, the non-executable ROS is accessed using sequential I/O operations, a bit like a tape.
Most notably, the non-executable ROS holds the interactive interpreters for the APL and BASIC programming languages. These are not “native” 5100 programs but were expressed instead in System/370 mainframe and System/3 minicomputer machine code respectively. The 5100 runs emulator programs for those computers in order to host the interpreters, so perhaps it’s just as well that the non-executable ROS is non-executable.
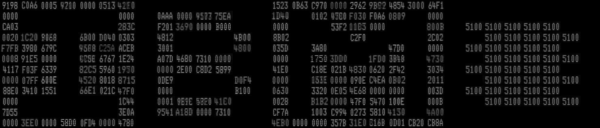
DATA
So this write-up is all about how the bits where pushed to the screen and recorded as pictures of the said screen. The characters in these pictures then where analyzed and with the help of machine learning the data could be successfully extracted. It is mind-boggling. And it is all on Github.